[#title_feedzy_rewrite]
If you own any cryptocurrency, you know you need a safe place to keep it because crypto is one of the most irretrievable assets if lost or stolen. This means having crypto wallets explained to you simply and clearly.
A crypto wallet is way different from the wallet or purse you keep your typical wallet—with cash and cards—in, it’s typically a software program on your computer or an app on your mobile device. Crypto wallets store crypto assets, but using them properly means keeping them and your coins safe.
In this guide, you’ll learn not only what the common wallets are but how crypto wallets work, which types are best for certain situations, and why it all matters. In the end, you’ll have a solid foundation that will go a long way toward keeping your crypto assets safe, whether you’re trading or HODLing.
What is a Crypto Wallet?
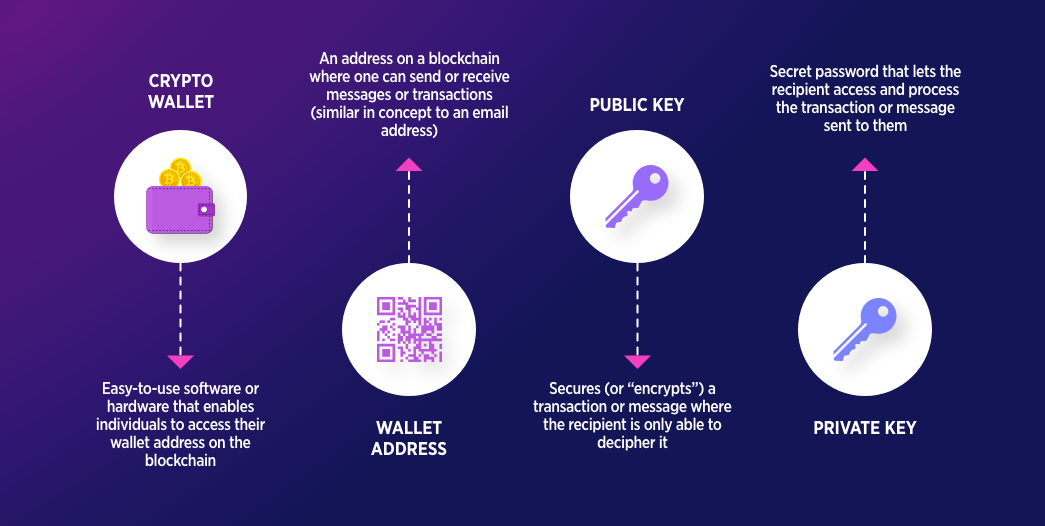
A crypto wallet is a digital interface that allows crypto owners to manage the public and private keys that are needed to interact with blockchains. Unlike traditional wallets that store physical assets, software wallets store private keys.
Private keys are long, complex strings of alphanumeric characters that prove ownership of specific on-chain assets. When wallet software first creates a new address, it generates a seed phrase, which is a unique phrase that can be used to recover the assets if you lose access to the actual physical device where the keys are stored.
Wallets connected to the internet also display the public key or public address associated with a particular wallet. These addresses are the publicly visible destinations on the blockchain where cryptocurrency is sent.
Why are Crypto Wallets Important?
The biggest thing that makes crypto wallets important is that they give you direct, explicit control over the digital assets stored in them without having to rely on banks, brokers, or other third parties.
When you hold your own private keys, you eliminate all counterparty risk. This means your assets are completely insulated from exchange hacks, account freezes, and similar unforeseen liquidity removal events. Wallets also provide the foundation for permissionless dApp access, so you can lend, borrow, trade crypto, or even mint NFTs in seconds, all by connecting your wallet to the appropriate platform.
Last but not least, wallets are the basis of crypto security measures. Cold wallets store private keys offline in cold storage, while “hot wallets” or online wallets secure private and public keys with two-factor authentication and biometric security measures. What it comes down to is that a crypto wallet is the cornerstone of non-custodial wallets and the first line of defense for your
How Do Crypto Wallets Work?
At their core, crypto wallets manage two critical pieces of information: a public key (your wallet address) and a private key (your digital signature). When someone sends you crypto, the transaction is recorded on the blockchain under your public address.
To move those funds elsewhere, you must prove ownership by signing the transaction with your private key. Wallet software handles this signing process behind the scenes, broadcasting the signed transaction to the network for validation. Because the private key never leaves your device, only you can authorize the movement of your assets.
How does a crypto wallet execute transactions?
- First, you’ll need to generate the transaction by entering the recipient’s address and the amount of crypto to send in your wallet’s interface.
- Next, your wallet will use your private key to create a signature to sign transactions by proving—mathematically—that you own those funds and are authorized to spend them.
- Now that the cryptocurrency transaction is ready, it’s broadcast to the blockchain network, where processing and validation nodes include it in the network.
- Notes then verify the signature against the public key, and provided it’s valid and the wallet balance is sufficient, the transaction is validated and accepted onto the blockchain.
- The transaction becomes part of the blockchain network’s ledger and is then used to confirm future transactions. Most transactions are not considered “complete” until they have a specific number of confirmations from the network.
Different Types of Crypto Wallets
The biggest difference in crypto wallet options is between custodial wallets and non-custodial wallets. Let’s take a look at what the differences are between these types of wallets and then look at some real-world examples.
Custodial Wallets
Custodial wallets are various wallets managed by exchanges or fintech services like Robinhood and Cash App. While they have a great user-friendly interface and feel like conventional online wallets, you are at the mercy of the provider’s security. If you lose access, your wallet provider can often restore it.
Source: Robinhood.com
Non-Custodial Wallets
Non-custodial wallets keep your private keys safe by giving you complete control over them. You generate your seed phrase, and you are responsible for keeping it stored offline. These wallets are true self-custody, and if you lose your private key, you will be unable to perform any blockchain transactions.
Custodial vs. Non-Custodial Crypto Wallets: Key Differences
| Feature | Custodial Wallets | Non‑Custodial Wallets |
| Key Control | Third‑party (exchange, service) holds keys | User controls private keys |
| Recovery | The provider can reset access | Only the seed phrase restores access |
| Ease of Use | Typically simple, account‑style login | Requires key management and backups |
| Risk | Counterparty risk (hacks, freezes) | Personal responsibility; loss of keys = loss of funds |
| Ideal For | Short‑term trading, for beginners who trust the provider | Long‑term holding, DeFi users, self‑sovereign ownership |
Hot Wallets
Hot wallets are software wallets that are connected to the internet.
- Desktop Wallets: Desktop PCs and laptops often have access to full-featured interfaces, local key storage, and even the ability to run a validation node. Ideal for users who want full on-device control.
- Mobile Wallets: Mobile wallets are common for Android and iOS, and these software wallets store private and public keys for fast access and on-the-go asset management in a simple digital tool. They typically have biometric or pin protection.
- Web Wallets: Web wallets are browser-based wallets or exchange account wallets that are accessible from just about any device. These are the peak of convenience but arguably the least secure option of all.
Cold Wallets
Cold wallets store your private keys offline, which reduces the potential attack surface to nearly zero.
- Paper Wallet: Paper wallets used to be a convenient way to gift Bitcoin wallets to people in the early 2010s to help it gain popularity. They are a printed sheet of paper with the public and private keys or a QR code that unlocks a wallet.
- Hardware Wallet: Hardware wallets are dedicated devices, like the Ledger Nano, that both generate and securely store keys in a tamper-resistant chip. Transactions are signed from within the device, reducing the potential for private key breach.
How are hot wallets different from cold wallets?
| Feature | Hot Wallets | Cold Wallets |
| Internet Connection | Online or frequently connected | Kept offline (air‑gapped) |
| Convenience | Instant access for daily use | Slower, best for long‑term storage |
| Security Risk | Vulnerable to malware, phishing | Immune to online hacks; physical theft risk |
| Typical Forms | Desktop, mobile, web extensions | Paper wallets, hardware devices |
| Ideal For | Small to medium balances, active trading | Large holdings, “HODL” investors |
Best Cryptocurrency Wallets Comparison
| Wallet | Wallet Type | Custody | Hot/Cold Wallet | Supported Chains* | Key Features |
| Ledger Nano X | Hardware | Non‑custodial | Cold | 1,000+ (BTC, ETH, SOL, etc.) | Bluetooth, Secure Element, staking, DeFi |
| Trezor Model T | Hardware | Non‑custodial | Cold | 1,000+ | Touchscreen, open‑source firmware, Shamir backup |
| MetaMask | Software | Non‑custodial | Hot | Ethereum, EVM chains | Browser/mobile, DeFi swaps, hardware‑wallet pairing |
| Coinbase Wallet | Software | Non‑custodial | Hot | Multi‑chain (ETH, SOL, etc.) | Built‑in DEX, NFT gallery, ENS support |
| Trust Wallet | Software | Non‑custodial | Hot | 70+ blockchains | Mobile, staking, in‑app swaps, dApp browser |
How to Secure Your Crypto Wallet?
- Keep your private keys offline, somewhere safe. If you don’t control the keys, you don’t control the coins.
- Always use 2FA or MFA on your hot wallets and exchange accounts.
- Never store seed phrases online. Keep them somewhere fire and flood-safe.
- Always use hardware wallets for larger portfolios.
- Keep multiple, redundant backups of your seed phrases in separate locations.
Best Practices for Crypto Wallet Management
- Segment Funds: Keep a spending (hot) wallet for daily use and a cold wallet for long‑term offline storage.
- Test Small Transfers: Before moving large sums, send a small test transaction to confirm the address.
- Stay Informed: Follow wallet provider announcements for security advisories or feature updates.
- Label Addresses: Use wallet labels or contact lists to avoid sending funds to the wrong account.
- Revoke Unused dApp Permissions: Periodically review and revoke token approvals to limit smart‑contract risk.
- Monitor Activity: Use explorers or portfolio trackers to watch for any unauthorized transactions.
- Practice Safe Browsing: Phishing attacks are incredibly common; install anti‑phishing browser extensions and avoid clicking on unknown links.
- Educate Trusted Contacts: If you share assets with family or partners, ensure they know recovery procedures.
Conclusion
Crypto wallets form the foundation of the self-custody crypto world and give you true ownership of your assets. They let you manage your crypto holdings as you see fit and without middlement. No matter which hardware or software wallets you decide to use, be sure you’re following security best practices and keeping all of your devices updated and patched to help protect your holdings long-term.
FAQs
Which crypto wallet is the best?
There’s no one‑size‑fits‑all answer. If you’re looking for peak security, hardware wallets like Ledger or Trezor are going to lead the pack. For everyday convenience, it’s hard to beat MetaMask or Coinbase Wallet, which both offer intuitive interfaces and multi‑chain support.
What is the best security wallet for crypto?
Hardware wallets provide the highest level of security because private keys stay offline. Ledger Nano X and Trezor Model T are industry standards for cold storage.
Can you convert a crypto wallet to cash? How do you cash out a crypto wallet?
Yes, you can easily convert a crypto wallet to cash. To cash out, you need to transfer your crypto from a personal wallet to a reputable exchange, sell it for fiat currency, and withdraw to your bank account. Some wallets also integrate on‑ramp/off‑ramp services for direct cash‑outs.
How to use a crypto wallet?
Download or set up the wallet, securely store your seed phrase, fund the wallet by receiving crypto to your public address, and sign transactions with your private key to send or interact with dApps.
Is a crypto wallet safe?
A wallet is as safe as its security practices. Non‑custodial wallets keep control in your hands, but you must safeguard the keys. Hardware wallets and strong operational security greatly reduce risk, whereas poor key management can lead to loss.
The post Crypto Wallet Explained: What It Is, How It Works, and Types appeared first on NFT Evening.

